Maybe you’re aware of the Office cloud policy service config.office.com where you can configure your Microsoft 365 Apps for Enterprise policies. If you select this strategy to configure the policies instead of using GPO’s, policies will be applied even on unmanaged devices. This is a huge benefit to combine the company security requirements and the flexibility to apply all configuration to any office apps and based on the user who is logged in to his office applications.
During rollouts, changes or even using an automated way for service providers, there is an API available but not pretty well documented (for not to say, not documented :-)). Let me know if you have any good links for that specific topic.
The first steps of all is to get the API backend URI and a Bearer token to authenticate with VS Code. Therefore you can use your browser in F12 mode or tools such as Fiddler Everywhere.
Browse to config.office.com within the new browser window and Sign in. Make sure that you have the proper permissions to use the App Admin Center. Required permissions: Global Administrator, Security Administrator, or Office Apps Admin.
To get the Bearer token, use the F12 Dev Tools from Edge Chromium or any other browsers or Fiddler. Start the Dev Tools, select Network clear the history an make sure you’re recording the network session.

Go to Policy Management on config.office.com. In the network recording, Headers, you will now see the Name “policy” where also the Bearer token is listed under authorization.

Copy the token to PowerShell or to VSCode and create a variable such as $accesstoken:
#Insert token from Browser
$accesstoke = @"
Bearer Bearer token here
"@Next, build your authHeather:
#Form request headers
$authHeader = @{
"Authorization"="$accesstoken"
"Content-Type" = "application/json"
}Your $authheader will look like this:
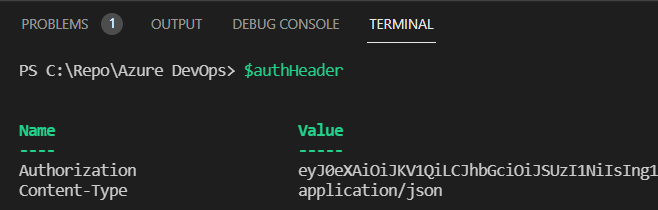
From here, you can use the token to request your policies or also to create new policies, depending of your role of course. Get all your current policies by using the Invoke-RestMethod command. As you can see in the example bellow, the API URI is https://config.office.com/api
#Get all Policies
$uri = "https://config.office.com/api/OfficeSettings/policies/"
Invoke-RestMethod -Method GET -Uri $uri -Headers $authHeaderResult:

In the next post, I will show you ho to create or update a policy using the -POST Invoke-RestMethod


