Today I played around with my Android device and Intune using the remote control option in Intune. The initial reason was, that my sister was calling me yesterday to help her out with her new Huawei Android phone. She tried to configure her Office365 account and was not able to do so. Of course, I helped her, but using remote control on the phone would be much cooler :-).
So I logged in to the Azure Portal, went to “Intune” and under Devices I found the Option “Setup” TeamViewer Connector.
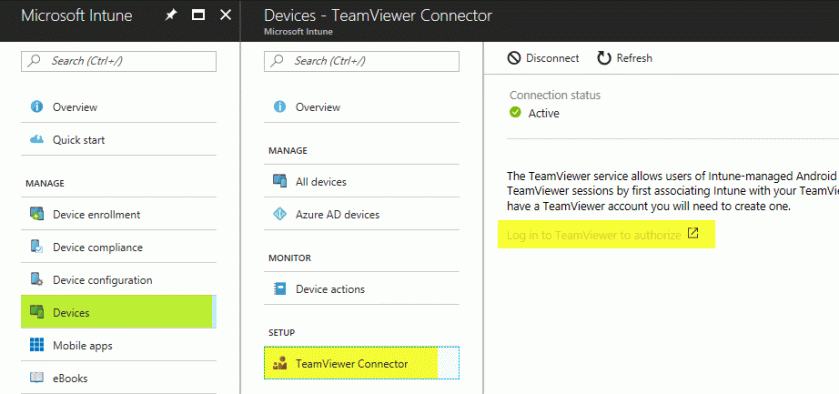
Before you can use TeamViewer to remote control your devices, you have to create an account or use an existing one to authorize Intune with TeamViewer. Go through the sign-in page from TeamViewer and authorize Intune. Make sure that the Connection Status in the portal is set to “Active”.
Don’t miss the message in the connector:
“The TeamViewer service allows users of Intune-managed Android devices to get remote assistance from their IT administrator. Create TeamViewer sessions by first associating Intune with your TeamViewer account and then authorizing it to work with Intune. If you don’t yet have a TeamViewer account you will need to create one. “
After that, It would probably make sense to deploy the Andoird TeamVewer Quick Support app to all Android Devices from your Company. This can be done by creating an app in the portal an assign it to the devices. This is not covered in this blog post.

How can you now initiate a remote session?
On your Windows 10 Desktop machine download and install (or just run) the latest version of TeamViewer. In my case it is TV 12. After that, sign-in to the application with the user account you created earlier in the post:

Go to the Intune Portal, select the device you like to remote control, go to Overview and there on the upper right hand you will find the three-dot option “…More”. Select “New Remote Assistance Session”.
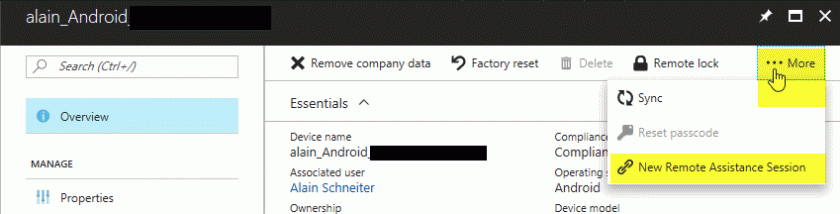
This will initiate a new session to your Android Device. Click “Yes”.
![2017-09-03 13_59_51-Dashboard - Microsoft Azure and 5 more pages -[InPrivate] - Microsoft Edge](https://blog.alschneiter.com/wp-content/uploads/2017/09/2017-09-03-13_59_51-dashboard-microsoft-azure-and-5-more-pages-inprivate-e2808e-microsoft-edge.gif?w=840)
The user will have to go to the Company Portal and accept the request. The request is displayed in the notifications area of the Company Portal App.

TeamViewer Desktop creates a new category for you called “Intune” with all your remote control requests out from Intune. Just double click the invitation you recieved and from there you’re able to remote control the users device.

Be aware that the user will need to accept and confirm the session again. Now you can remote Control the Android device out from your TeamViewer Software. Very cool.
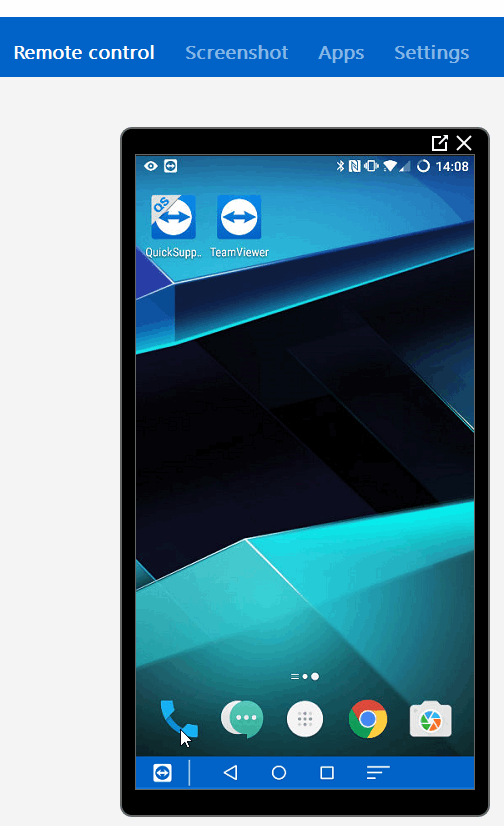
A great and nice option which should be used for remote supporting your android devices!