Windows 10 Current Branch (1607 & 1703) is using a default drive encryption of XTS-AES 128 if you encrypt the disk during OSD using ConfigMgr Current Branch.
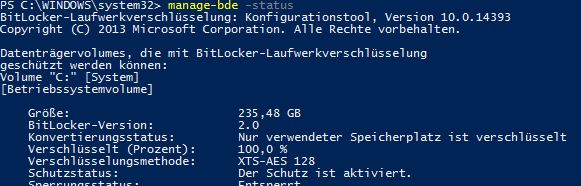
Command above: manage-bde -status
Some customer maybe have the requirement to change the default to a different mode like XTS-AES 256.
This can be changed using a GPO or CIs in ConfigMgr but then you have first to decrypt the disk, assign the new policy and encrypt the disk again. This is annoying and not very user & admin friendly.
Since a while ConfigMgr is using an option called Pre-provision Bitlocker. This step in the TS is encrypting only the currently used diskspace. As it is in WinPE this is a very small part of the disk and also a quick step. But this step is using the command “manage-bde.exe -on C: -used” and you are not able to change the encryption method.
Solution
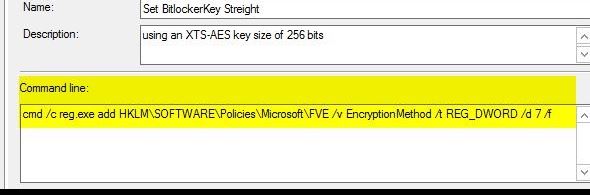
To change the method to XTS-AES 256 or a different method, use following registry key just before the Pre-provision BitLocker step:
cmd /c reg.exe add HKLM\SOFTWARE\Policies\Microsoft\FVE /v EncryptionMethod /t REG_DWORD /d 7 /f
The DWORD value 7 ist setting the method to XTS-AES 256. Use the list bellow to assign a different method:
Value 3, AES_128:
The volume has been fully or partially encrypted with the Advanced Encryption Standard (AES) algorithm, using an AES key size of 128 bits.
Value 4, AES_256
The volume has been fully or partially encrypted with the Advanced Encryption Standard (AES) algorithm, using an AES key size of 256 bits.
Value 6, XTS_AES128 *
The volume has been fully or partially encrypted with the Advanced Encryption Standard (AES) algorithm, using an XTS-AES key size of 128 bits. – This is the default of Windows PE 10.0.586.0 (1511 Release)
Value 7, XTS_AES256 *
The volume has been fully or partially encrypted with the Advanced Encryption Standard (AES) algorithm, using an XTS-AES key size of 256 bits.
* Only supported for deployments of Windows 10 images build version 1511 or higher
The Task Sequence step I used is a command line and is configured to run just before “Pre-provision” BitLocker:
This has been testet with the Windows 10 Enterprise Builds 1607 (Anniversary) & 1703 (Creators).

I’ve found that on Windows 10 1703 using the key value “Encryption Method” causes the task sequence step to fail. MBAM policy creates the value as “Encryption MethodWithXtsOs” but although the step completes successfuly that the pre-provision step ignores it. Do you experience the same behaviour?
LikeLike
Hi Ben, no we do not. Do you have any SMSTS.log entires for that? Thanks, Al
LikeLike
There seems to be some inconsistency in the results of using “Encryption Method” and “Encryption MethodWithXtsOs”, I am deploying Windows 10 1703 in ConfigMgr 1706 with MDT Integration and saving BitLocker Recovery to AD until MBAM is implemented, the BitLocker Pre-provision step did not work with the “Encryption MethodWithXtsOs” registry option, but did when I added the “Encryption Method” registry option.
Subtle changes and reversions seem to be implemented without adequate documentation from Microsoft.
LikeLike
Hi Akin,
I’m not seeing this “issue” with Windows 10 1703 or/and CM1706. But thanks for your workarround!
Regards,
Al
LikeLike
That’s good to know. Am curious: Al, I see you’re only encrypted used disk space but will the Pre-Provision step also support FDE or will it ignore the associated keys?
LikeLike
It did work for me, i got some registry file to import before enable bitlocker to make it 256, but your works save my time,
Thank you
LikeLike
Thanks for that, Can you post your regfiles? Do you use Windows 10 1709 or a different build?
LikeLike
I hope everyone (including the author of this article) realizes that changing the registry as outlined will NOT change the method of BitLocker encryption used on drives that are already partially or fully encrypted with BitLocker. All it will do is change the default encryption scheme used in the future. This is not open for debate–Microsoft explicitly states this, and it should be intuitively obvious to begin with.
LikeLike
Hi Todd, I hope all the readers are aware of that. However, if you have encrypted a drive with 128 bit, there is no way just to “switch” to 256 bit. Except un-ecrypt and re-encrypt the drive again with another policy (MEM) applied.
Thanks,
Al
LikeLike