Hi – It’s me, Al
Blog post updated: July 19th 2017
Remote Desktop Services (RDS) on Windows Server 2012 R2 is now on market since a while. Let’s have a look at the 2012 R2 Certificate configuration (for a Lab).
First we have to create a template on the internal Certificate Authority (CA). We use a Workstation Authentication Template for that. Open your CA Manager – Cartificate Templates – Manage
Duplicate the “Workstation Authentication” Template.
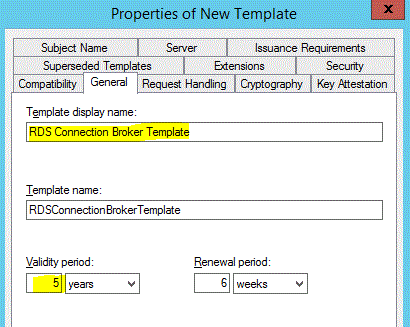
Change the Template Display Name to a friendly name like “RDS Connection Broker Template ” and also Change the validity period to 5 years
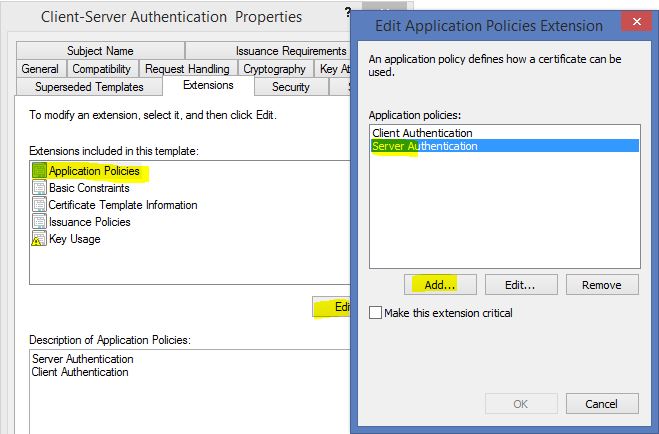
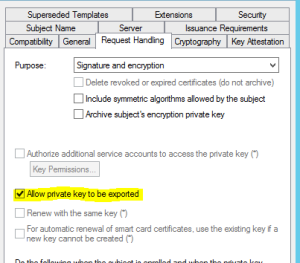
On the “Extensions” tab select “Appliaction Policies” and click “Edit”. Add the “Server Authentication” to the policies
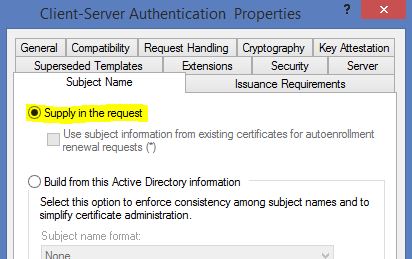
On the “Subject Name” tab Change the Option to “Supply the request”.
Make sure the Private Key is exportable as this is needed from the Connection Broker Server itself.
Depending on the security in your organization, change the template security. Probably you have to add the Connection Broker Servers to allow the enrollment of the certificates. Best is to use an Active Directory Security Group.
As soon you have created the template, you have to request the certificate using the certificate mmc from one of the Connection Broker Server. If you have only one or two Connection Brokers, it’s maybe easier to add the Subject Alternate Names to the Certificate.
In a lasrger envoirnment it is recommended to use a wildcard certificate issued by your corporate CA. We will request a wildcard certfificate also for the lab environment.
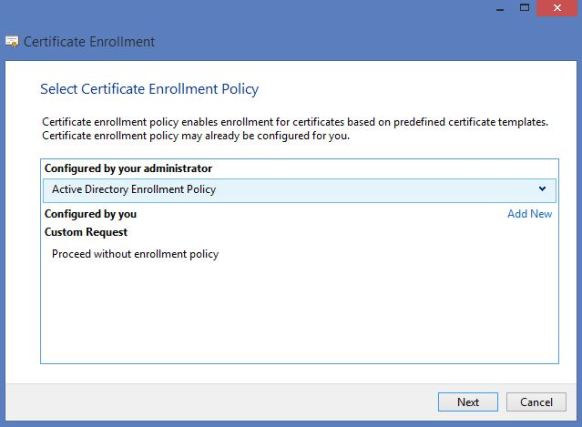
Open the certificate mmc from a RD Connection Broker Server. Go to Personal – Certificates – All Tasks – Advanced Operations – Create Custom Request … . The Request Wizard will Launch
Select Active Directory Enrollment Policy – Next
Select the “RDS Connection Broker Template ” (or whatever you called it) which we have created earlier in the Deployment. Leave the request format default.
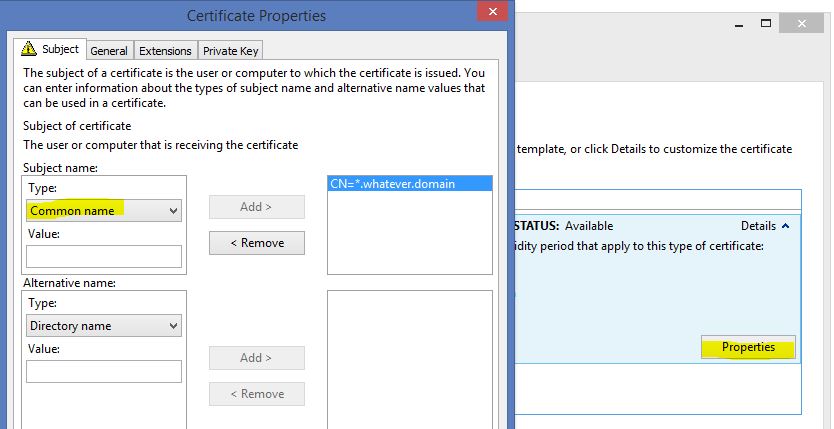
Change the following properties on the “Subject” tab:
Subject Name: “Common Name” add your Domain
Change the following properties in the “Private Key” tab:
Private Key: Select “Make private Key exportable”
Apply the Settings and finish the Custom request.
Now you have to export the certificate for your Connection Broker Server. Open the certificate MMC (local computer) from your Connection Broker Server – navigate to Certificates – Personal – select the newly created certificate – All Tasks – Export
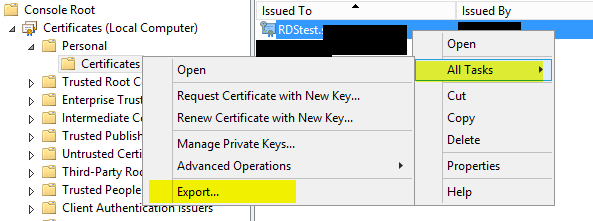
Go trough the wizard and use the following options:
Private key = Export
PFX = Standard Options
Password: required
Save as: PFX
Go to your RDS Deployment – Select “Edit Deployment” – Select “Certificates”
“Select existing cerificate” and use you’re previous saved *.pfx file. Enter the password you gave and select the option to save the certificate in to the Trusted Root store. Apply this Settings for each Connection Broker Publishing and SSO. You have to do this for each role service seperate.
All your Connection Broker Certificates should now be in a Trusted state:
For the Web faced roles such as “Web Access” and “Gateway”, we recommend to use a 3d Party public cerificate authority (GoDaddy, StartSSL, etc.)
Hope this helps. Let me know if you have any questions.
Cheers, Al








thanks so much, worked fine! 🙂
LikeLike
Hi Guys,
Would you recommend having a 3rd party cert for the connection brokers as well? Been looking online for the correct answer but am struggling to find the right one for RDS 2012.
Our situation is that we have the gateway servers, then two cbs in a HA sitting below the GWs. If we don’t have a proper cert on the CBs will our clients get cert warnings etc when running the apps?
Thanks
Steve
LikeLike
Hi Steve,
External clients would only connect to RDWeb and RD Gateway using an external name. Those two roles need to have a certificate that matches the external name (from a puclic CA). A certificate for Single Sign On that matches the internal names should work just fine provided you are using RDP 8 to connect.
Make sure you change the Published Name of the Connection Broker using the script from TechNet Gallery: https://gallery.technet.microsoft.com/Change-published-FQDN-for-2a029b80
Hope this helps. Let me know if you have further issues!
Cheers, Al
LikeLike
That’s great thanks Al, I’ll give it a go tomorrow.
LikeLike
Great, let me know. Cheers, Al
LikeLike
Awesome post, the one place I found that had all the info in one place!
Thanks a million!
LikeLike
Hi, thanks for the info, it allowed me to get the web interface working (except for getting the “do you trust the publisher popup) but I can’t setup a remoteapp connection on the client. It tells me there is a problem with the connection’s security certificate. I’m not sure what I missed.
LikeLike
Hi Zack,
Usually this is an issue with Connection Broker RD Published name. Could you change that to your public name? See the proper answer on TechNet: https://social.technet.microsoft.com/Forums/en-US/de848101-7414-40d5-bce5-eadffd20140e/certificate-error-when-connecting-to-remoteapp-outside-of-private-network?forum=winserverTS
Let me know if this helps,
Regards,
Al
LikeLike
Thanks for the reply. It’s actually on my internal network that I’m having the issue.
LikeLike
Dosen’t matter. This should also be done on the internal network.
1. Create a DNS Name for the RDConnection Boker. If you use more than one, ceate round robin entries.
2. Run the script and point it to the DNS record
3. The CB certificate neets to contain the rdcb FQDN of the DNS entry
4. Assign the cert. This cert will sign the remote apps
5. Create the GPO to trust the thumbrpint
Let me know if you have questions.
Cheers,
Al
LikeLike
Thanks for the help Al. I will definitely make sure those things are implemented. The solution to my immediate problem… I wasn’t using the FQDN to make the connection *face palm*
LikeLike
Right at the top of this article, you say to duplicate the Server Workstation Template, but I din’t see any such template in the list. There is a Computer Template and a Workstation Template, but no Server Template. Which is the right one ?
LikeLike
Sorry for the delay on that. This is a mistake and I will change it. As you can see in the screenshot, it is the Client-Server Authentication Template which you have to duplicate. Cheers, Al
LikeLike
Thanks for the reply.
I don’t understand how that can work, either. If the name of the original template and the new one are the same (as per your instruction immediately following the ‘duplicate’ step), firstly the name of the template would be ‘copy of …’, and changing that to the original would overwrite it, and secondly the name would not be highlighted as it is in the screenshot, which it would be if you were about to change it, but the screenshot shows the name you directed that it be changed to.
I suspect that since the steps are so automatic to you, having done this several times, there might be a few that went by too fast for me to follow.
If you could add a few screenshots and verbiage, I would love to make this work.
Thanks for your help.
LikeLike
Agreed with Joshua. Pls. be advised that this post is not complete. It may help those who just need a little push, but it is lacking a few vital steps.
LikeLike
Hi Pete,
Please let me know where you stuck.
Cheers,
Al
LikeLike
I am having issues exporting the certificate to PKCS #12 .pfx file – the option is greyed out
Also I found a couple of missing steps 1) in the CA mmc right click on Certificate Templates > New > Certificate template to issue (otherwise you are unable to use the new template) and also 2) the default validity period in the registry is 2 years – you need to use “certutil -setreg caValidityPeriodUnits 5” to set to 5 years and then “net stop certsvc” & “net start certsvc” to restart certificate services
LikeLike
Having the same issue, was this resolved?
LikeLike
Hi, this does not work for me. I have no issues following the steps until I go to the CA server and try to submit the request. I get a popup saying “The requested certificate is not supported by this CA. 0x80094800 (-2146875392 CERTSRV_E_UNSUPPORTED_CERT_TYPE). Denied by Policy Module 0x80094800, The request was for a certificate template that is not supported by the Active Directory Certificate Services Policy:
1.3.6.1.4.1.311.21.8.5878923. and a bunch more numbers.
Any ideas? Also, do I need to use a wildcard cert or can be just for that server name?
Thanks
Paul
LikeLike
Hi Paul, have you used the 2003 compatibility version of the template you created?
You no not need to use a wildcard, but then you need to add the RDS Connection Broker Server Name to the cert. if you use RD Conneciton Broker in HA mode, make sure you add the round robin name of the the RDCB Servers.
I have deployed RDS certificates like this on Monday and it worked well.
Let me know if you need more help.
Cheers,
Al
LikeLike
I cannot export the certificate to PKCS #12 .pfx file – the option is greyed out
LikeLike
hello,
I have the same problem, where I did the same steps but still telling me that the request is not supported. please, can you explain in detailed steps how to solve this problem? Sorry, I am new to the certificate.
LikeLike
I had the same error. The missing step in this article is that you have to add the created template to the CA. So after creating the template, right click Certificate Templates folder in the CA mmc, choose New -> Certificate Template to Issue, select the created “RDS Connection Broker Template” and click OK. Now you can succesfully finish the certificate request.
LikeLike
I can’t export the certificate to PKCS #12 .pfx file – the option is greyed out. Did I miss something?
LikeLike
HI Al, thanks for the right up. I think I am pretty close to having this working, but my clients aren’t getting the certificates. My connection broker has the cert and shows that it is trusted. However, when I setup a remote connection on a desktop in the control panel I am getting the error that there is a probably with this connections security certificate. Do I need to manually copy the cert to the PC or is there a way to automate this?
LikeLike
Depends. If you have a internal CA the root certs will be deployed from there. If you use a self-signed, then you have to import them to the computers personal certifcate store.
You can use GPO to reach your goal.
Cheers,
Al
LikeLike
Thanks for your response.
I do have an internal roots server, but that doesn’t appear to just automatically provide a cert. I also tried the self-signed cert without luck as well. From a Windows PC i get the certificate error when I connect to the webserver or if I go through the remote desktop connections applet in the control panel. Once I can verify that this is working I can setup the required Policies to push this out to the clients as needed. However, I am also trying to get this to work with a Linux based Wyse client, which isn’t working as well. So I will need to find an alternate method to deliver the cert those devices as well.
LikeLiked by 1 person
Can you confirm that the Windows 8/10 Client has the root and sub certs installed? When you go to the RDWeb Site, select the certificate in the browser address bar and check the chain.
Does the cert contain the rdweb name of the url? If you use an url like rdweb.contoso.com the cert must contain ether *contoso.com or rdweb.contoso.com as a SAN entrie.
The Control Panel applet is not working as long you get cert missmaches on the “normal” webpage.
As far as I know, Linux Wyse do not support RDP. Or do you have an Wyse which supports RDP and not only PCoIP?
LikeLike
I am actually using Windows 7 ultimate. I may be asking simple questions, but I don’t want to assume anything. I believe that I have the root and sub certs installed, but what is the best way to verify? They are showing up in the personal and trusted roots on the client when I look at the certificates in MMC for the local computer. Right now they were added manually and not by GPO, but I will change that in the future. The cert does contain the wild card name of *.domain.local.
As far as the Linux WYSE devices I am using, they are Dell Z50D’s, which do support RDP. My final implementation though will probably use a similar device running Microsoft embedded for ease of use.
LikeLike
Where is the Base64 request saved to? I don’t know where to get the request file when I go to Open the CA MMC – right click the Root CA – All Tasks – Submit new request… Select the certrequest you have saved (where did the file save to as there was no prompts in the previous step to specify a location) What am I missing here?
LikeLike
Turns out you have to give the certificate a friendly name under the General Tab of Certificate Properties otherwise you don’t get the tab to browse when saving it.
LikeLike
Hi Pierre,
Sorry, I have updated the post. Give another try.
Cheers,
Al
LikeLike
Reblogged this on Konkretor Blog, IT Stuff and more.
LikeLike
After “Apply the Settings and finish the Custom request.” I have a .req file and no cert. Either I’m missing something or there is a step between the .req file and the cert file missing.
LikeLike
Hi Zach, did you create the template and raised a request of the cert from your connection broker? Then you should have a proper cert in the personal store of the CB now. This you can export. Let me know if that helps.
LikeLike
Hello, I have the same “problem”. After the step “Apply the Settings and finish the Custom request.” I get a screen in the wizard where I have to choose a location for the .req-file. Even after a day after creating the custom template for the certificate. I double and triple checked every step for the creation of the template. This test setup is on Server 2016.
LikeLike